고정 헤더 영역
상세 컨텐츠
본문
1. 본사와 지점간 특정 PC만 IPsec IKEv1 VPN 통해 본사의 WEB, WAS 서버에 연결 요청
- 본사 : ASA5516X
- 지점 : C1905 (security License 필요)
- 지점 네트워크는 192.168.2.0/24 이고 192.168.2.0 255.255.255.240 대역만 본사 접속 가능
- ASA Mgmt0/0은 192.168.80.11로 ASDM 연결

2. 본사 ASA와 WEB / WAS IP설정
| # WAS interface Vlan1 ip address 192.168.136.2 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.136.1 # WEB interface Vlan1 ip address 192.168.36.2 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.36.1 |
| # HQ_ASA (Basic) interface GigabitEthernet0/0 nameif outside security-level 0 ip address 100.100.100.1 255.255.255.0 no shut ! interface GigabitEthernet0/1 description ### WAS SERVER ### nameif inside security-level 100 ip address 192.168.136.1 255.255.255.0 no shut ! interface GigabitEthernet0/2 description ### WEB SERVER ### nameif dmz security-level 100 ip address 192.168.36.1 255.255.255.0 no shut ! interface Management0/0 management-only nameif management security-level 100 ip address 192.168.80.11 255.255.255.0 ! route outside 0.0.0.0 0.0.0.0 100.100.100.3 ! object network WEB subnet 192.168.36.0 255.255.255.0 ! object network WAS subnet 192.168.136.0 255.255.255.0 ! object-group network BRANCH network-object object WAS network-object object WEB ! object network STAFF_LAN subnet 192.168.2.0 255.255.255.0 ! http 192.168.80.0 255.255.255.0 management ! username admin password cisco ! policy-map global_policy class inspection_default inspect icmp ! end |
| # HQ_ASA (IPSec) - CLI 사용할 경우 crypto ikev1 enable outside crypto ikev1 policy 1 authentication pre-share encryption aes hash sha group 5 lifetime 86400 ! tunnel-group 100.100.100.3 type ipsec-l2l tunnel-group 100.100.100.3 general-attributes default-group-policy GroupPolicy_100.100.100.3 tunnel-group 100.100.100.3 ipsec-attributes ikev1 pre-shared-key CISCO123 ! access-list outside_cryptomap extended permit ip object-group BRANCH object STAFF_LAN ! nat (any,outside) source static BRANCH BRANCH destination static STAFF_LAN STAFF_LAN no-proxy-arp route-lookup ! crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac ! crypto map outside_map 1 match address outside_cryptomap crypto map outside_map 1 set peer 100.100.100.3 crypto map outside_map 1 set ikev1 transform-set ESP-AES-128-SHA crypto map outside_map interface outside |
# HQ_ASA (IPSec) - ASDM 사용할 경우     - Pre-shared Key는 위에 설정한 CISCO123 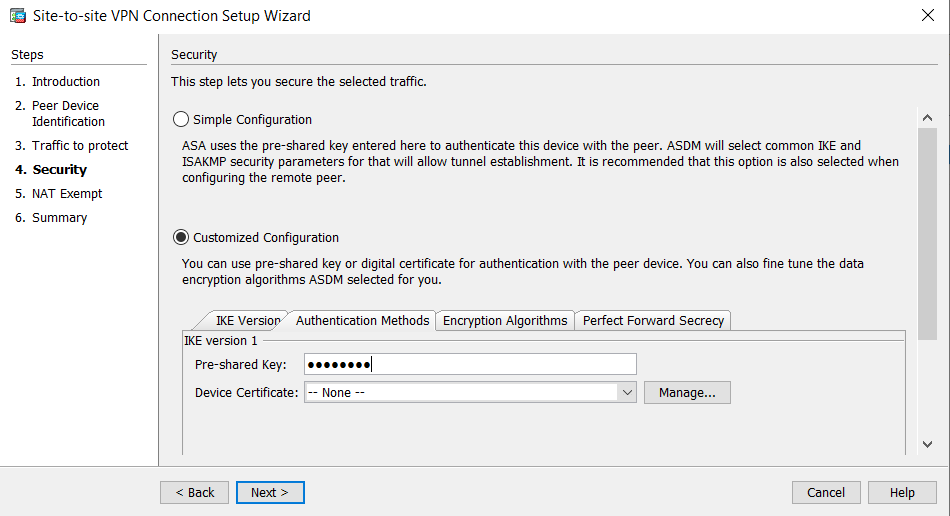     |
- 검증
 |
3. 지점 라우터의 사용자 NAT 및 DHCP 설정
| # Branch_R1 ip dhcp excluded-address 192.168.2.1 192.168.2.15 #특정 사용자는 DHCP 대역 열외 ! ip dhcp pool LAN network 192.168.2.0 255.255.255.0 default-router 192.168.2.1 dns-server 8.8.8.8 lease 0 8 ! interface GigabitEthernet0/0 ip address 100.100.100.3 255.255.255.0 ip nat outside ! interface GigabitEthernet0/1 ip address 192.168.2.1 255.255.255.0 ip nat inside ! ip nat inside source list NAT-POOL interface GigabitEthernet0/0 overload ip route 0.0.0.0 0.0.0.0 100.100.100.1 ! ip access-list extended NAT-POOL permit ip 192.168.2.0 0.0.0.255 any |
| # Branch_SW interface Vlan1 ip address 192.168.2.2 255.255.255.0 ! ip route 0.0.0.0 0.0.0.0 192.168.2.1 |
- 검증
# DHCP_PC |
4. 지점 라우터의 VPN 설정 (반복 설정하며 내용 숙지)
| # Branch_R1 (VPN 설정) crypto isakmp policy 1 encr aes authentication pre-share group 5 crypto isakmp key CISCO123 address 100.100.100.1 ! crypto ipsec transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac mode tunnel ! crypto map outside_map 1 ipsec-isakmp set peer 100.100.100.1 set transform-set ESP-AES-128-SHA match address VPN-POOL ! ip access-list extended NAT-POOL # 인터넷 일반 사용자를 위한 NAT POOL 9 deny ip 192.168.2.0 0.0.0.15 192.168.36.0 0.0.0.255 # WEB 접속을 위한 VPN 사용자는 NAT 필요없음 9 deny ip 192.168.2.0 0.0.0.15 192.168.136.0 0.0.0.255 # WAS 접속을 위한 VPN 사용자는 NAT 필요없음 ! ip access-list extended VPN-POOL #특정사용자를 위한 VPN POOL permit ip 192.168.2.0 0.0.0.15 192.168.36.0 0.0.0.255 # WEB 접속을 위한 VPN 사용자 IP permit ip 192.168.2.0 0.0.0.15 192.168.136.0 0.0.0.255 # WAS 접속을 위한 VPN 사용자 IP ! |
- 검증 1
# VPN_PC에서 static IP를 설정후 ping 통신 확인 # Branch_R1에서 VPN 연결 확인  |
- 검증 2
# STAFF_PC에서 DHCP로 IP를 받은 후 ping 통신 확인 |
- 검증 3
# ASA에서 IPSec 모니터링 탭 확인하여 트래픽 확인 |
============================================================================
# TIP : Branch_R1 전체 설정 첨부
  |
'보안' 카테고리의 다른 글
| [EVE-NG] ASA - Site to Site VPN between ASA (2부) (0) | 2020.01.24 |
|---|---|
| [EVE-NG] ASA - 외부에서 ASA(방화벽) DMZ 접속 (outside to dmz) (0) | 2020.01.09 |
| [EVE-NG] ASA - Site to Site VPN between FTD (Using FMC) (0) | 2020.01.08 |
| [EVE-NG] ASA - Site to Site VPN between ASA and FTD (Using FMC) (0) | 2020.01.08 |
| [EVE-NG] ASA - FTD 기본 설정 및 Timezone (Using FMC) (0) | 2020.01.06 |




